- Details
-
Published: Sunday, 06 December 2020 20:47
The control stability of the feedback loop in DC/DC converters is a quite important subject in power electronics. However, its importance is often lost as the analysis becomes very theoretical, because of all the math that accompanies it. Simulations and experimental tests can always show more pragmatic results about how the theoretical calculations affect the behaviour of the converter during step load changes.
A typical DC/DC converter controller samples the output voltage, compares it with its reference and alters the duty cycle accordingly, to minimize the error between the two values. The components placed on this feedback loop (low power resistors and capacitors), together with the power components characteristics (e.g. LC filter, converter topology) determine the converter stability and response during step changes. The purpose of adding compensation to the error amplifier is to counteract some of the gains and phases contained in the control-to-output transfer function that could jeopardize the stability of the power supply.
The control theory suggests that for a good loop compensation, the gain margin must be positive, the phase margin between 45 to 60 degrees and the gain curve should have a slope of -20dB/decade at the crossover point. But it's also significant to understand what would the result be if no proper compensation is applied. I have used a full-bridge DC/DC converter, controlled by an ADP1055. The IC samples the output voltage and changes its PWM duty cycle accordingly, based on a Type III network. The filter is digital and can be modified through a GUI, so tests with different loop network settings are almost instant.
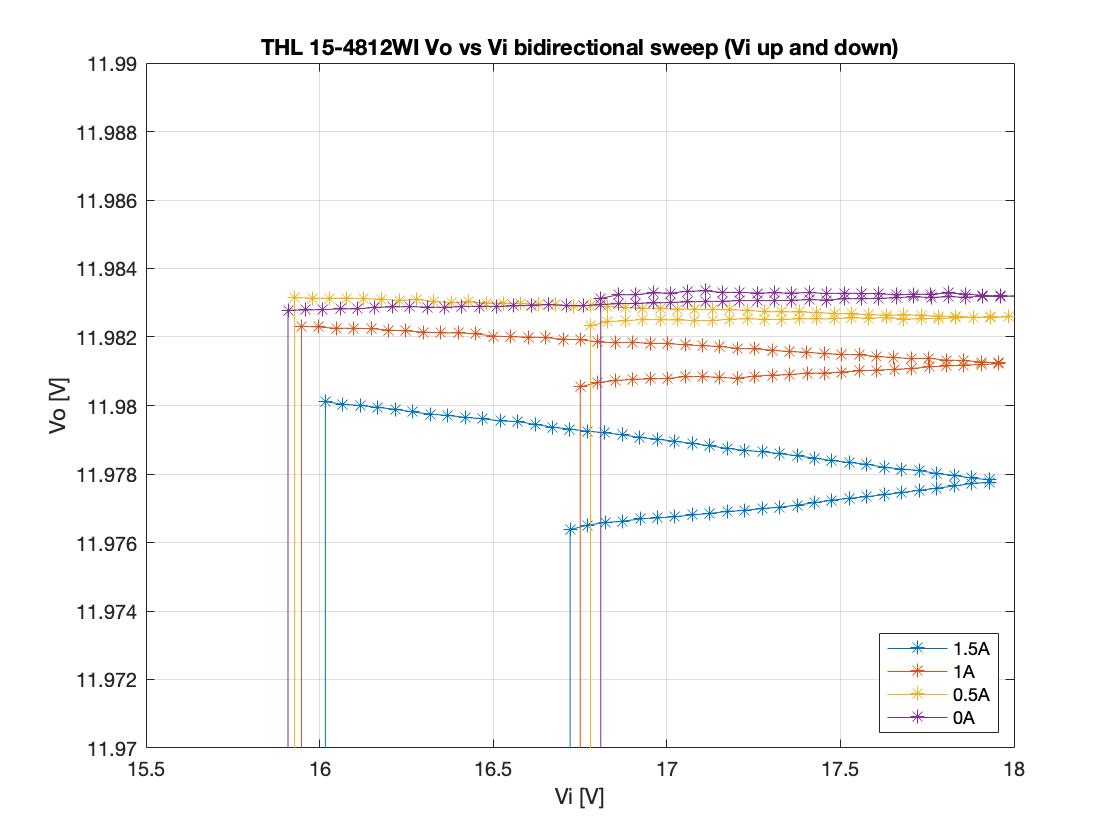
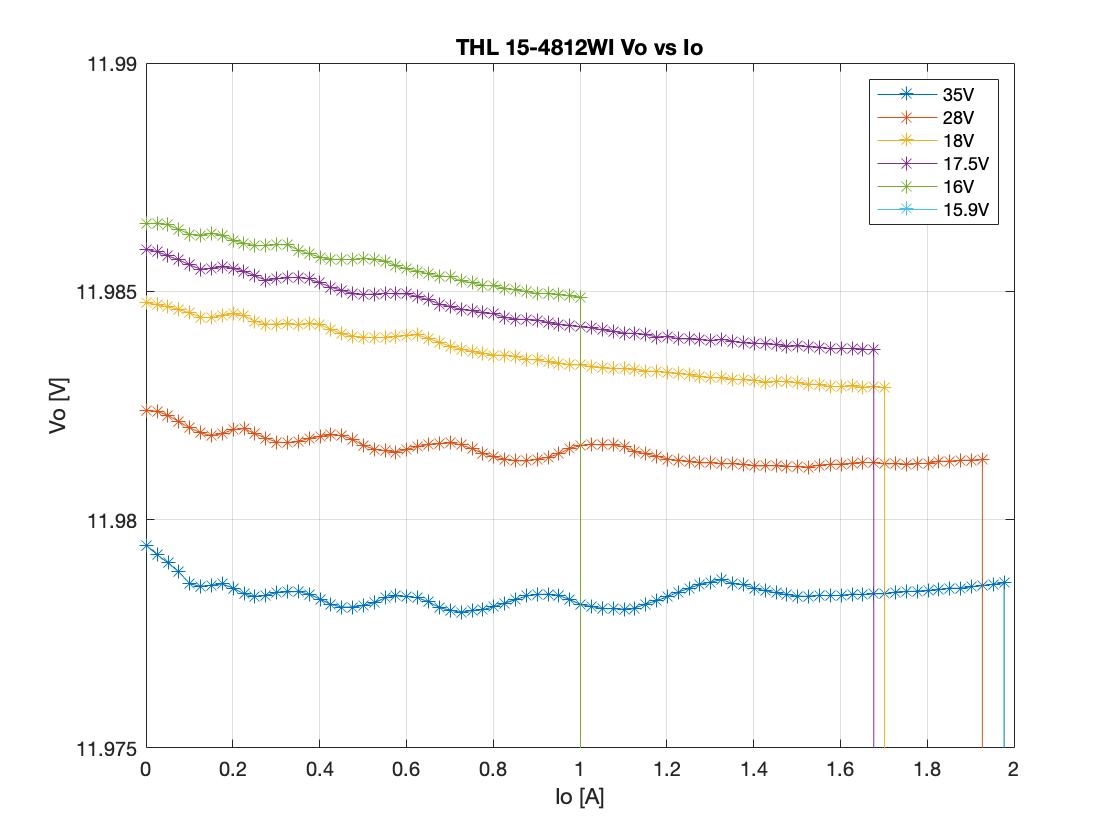
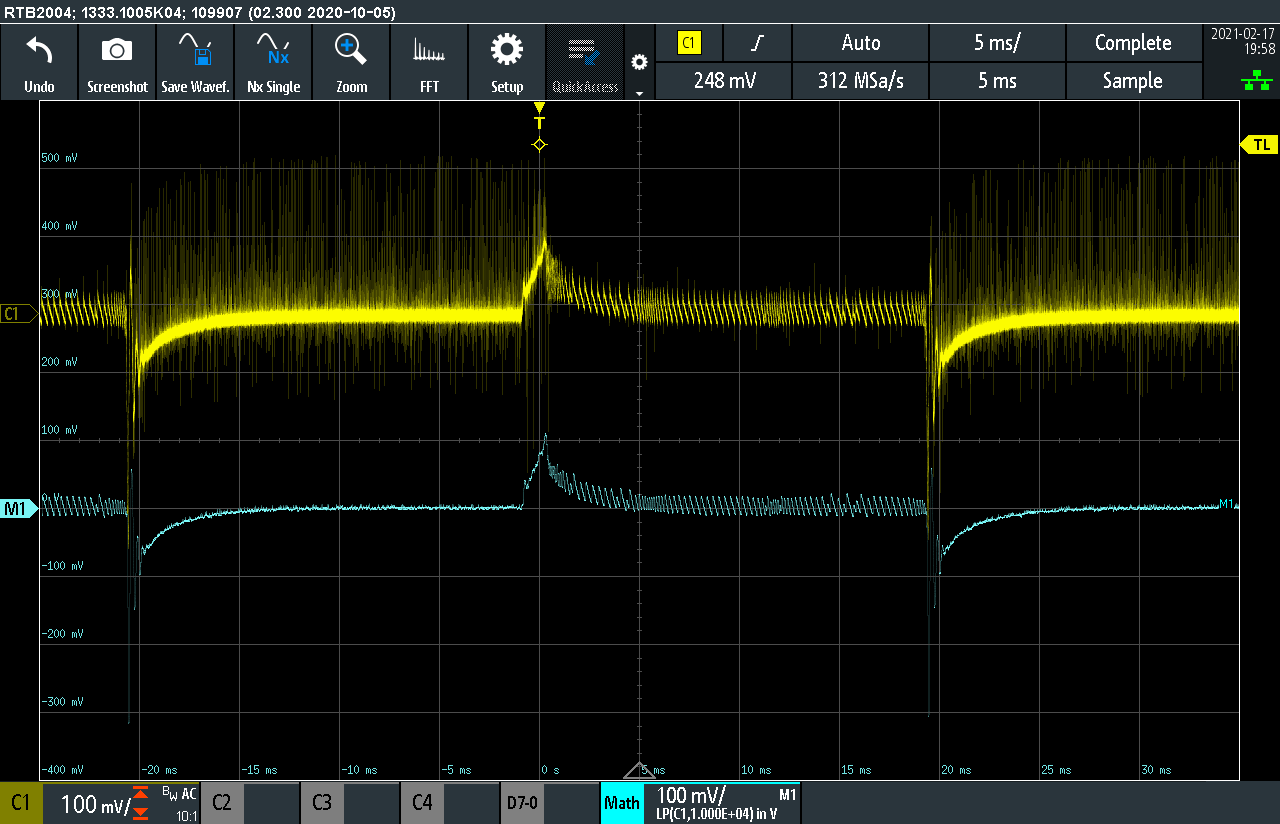
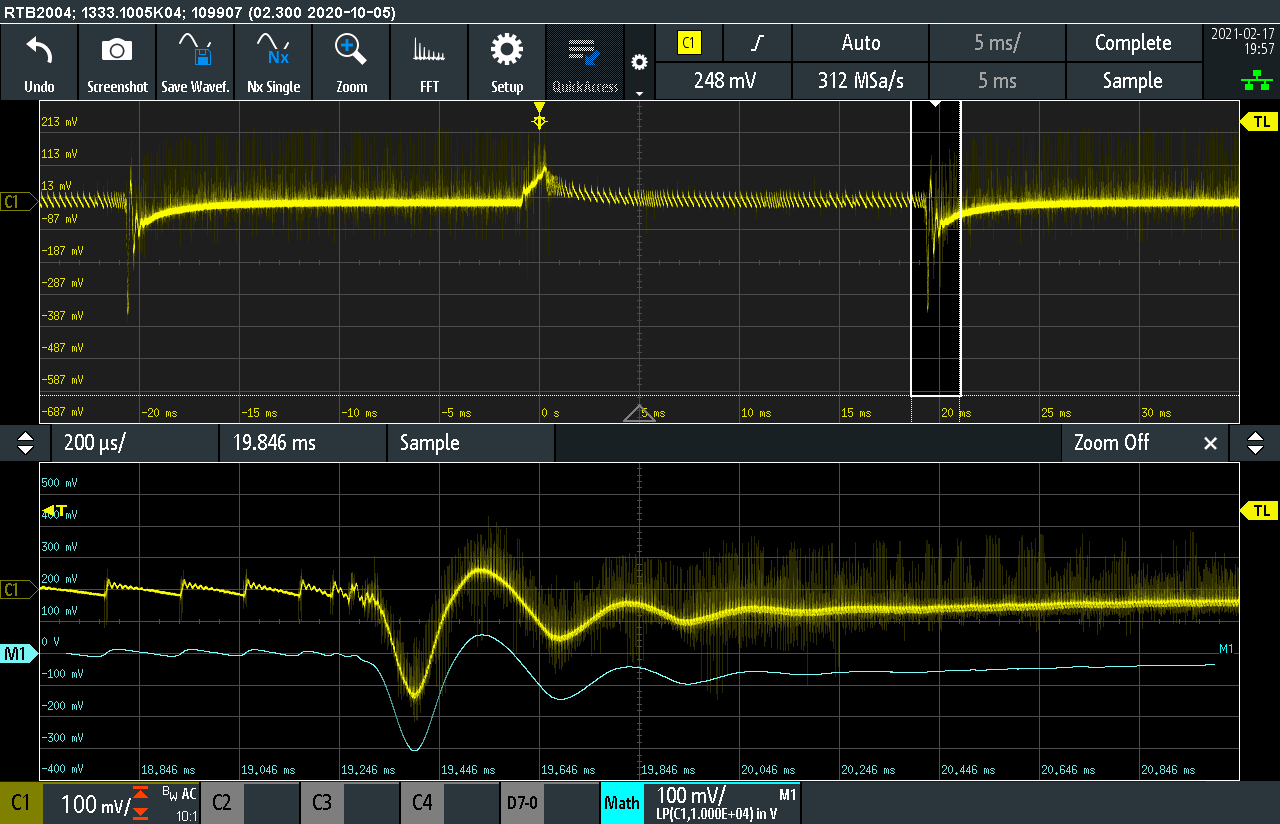
The PWM frequency for all the tests below is 125kHz and the output voltage is sampled once per PWM cycle. A step change of 2A to 15A (10% to 75% of nominal output) and back to 2A is conducted using an electronic DC load. The input side transformer current, as well as the output voltage are measured on the oscilloscope. A 10kHz low-pass filter is applied on the voltage output measurement, for clarity. The GUI settings are shown below. The pole/zero locations of the compensation network can be altered. The GUI automatically calculates the full system frequency response, as well as the gain/phase margins.

Examples of insufficient compensation
Low DC gain
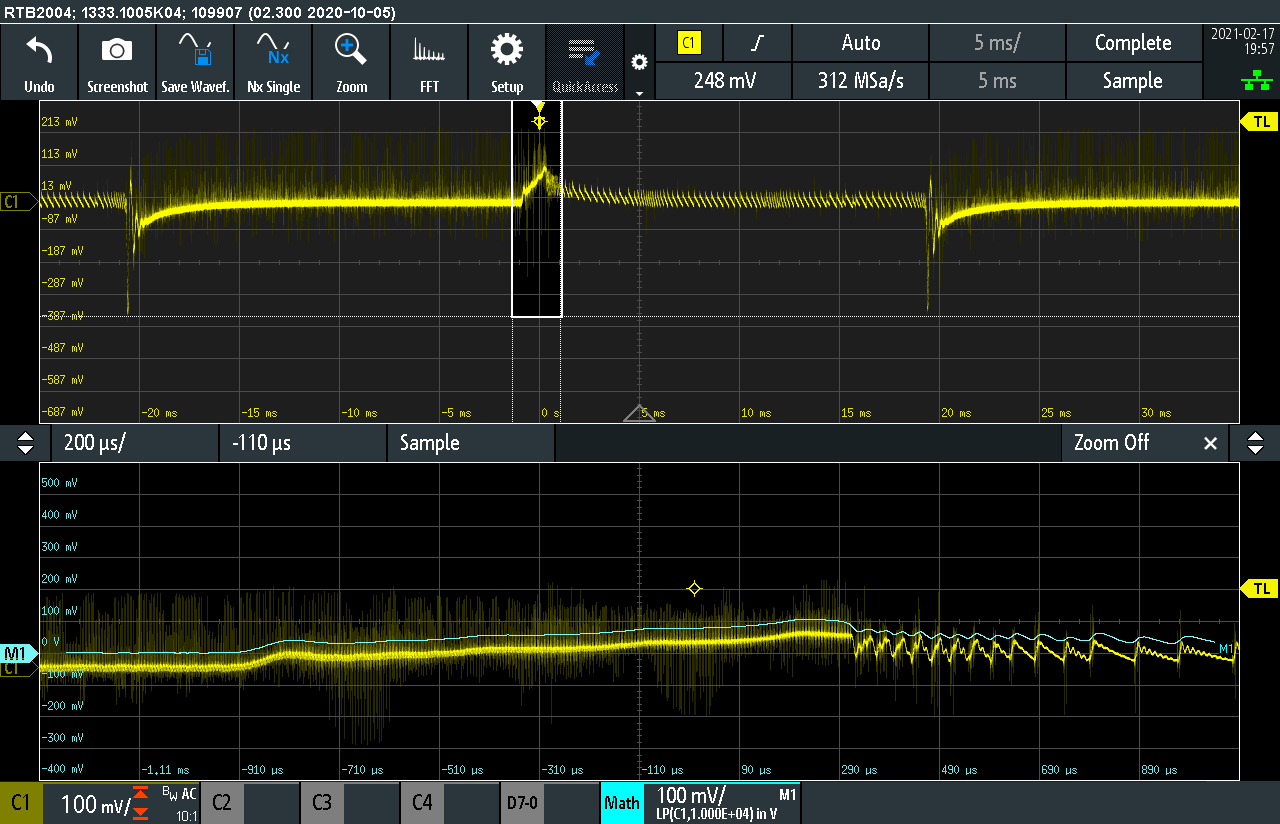
The figures below show the step response of a system which has a low DC (sometimes also called low frequency) gain. Although there is no overshoot on the voltage and the gain/phase margins follow the guidelines, the response is severely overdamped, causing a steady state error which goes to zero after many switching periods.


Underdamped
An opposite response is the one shown below. Notice that both gain and phase margins are negative, something that can cause oscillations to the output voltage and may lead to instability. As can be seen, 5 or more oscillations take place before the voltage reaches steady state.


Oscillation
Here is another example of a high loop compensation gain which causes oscillations. Although again, the gain and phase margins do follow the guidelines, the high gain and high crossover frequency cause the system to exhibit a permanent oscillation on the output voltage. This is an unacceptable behaviour on a converter operation.


Low margin
The control theory recommends a phase margin above 45 degrees and a gain margin above 3dB. The setup below does not respect any of the two recommendations. However, as can be seen the system exhibits an almost ideal response with a critically damped oscillation, very low overshoot and undershoot, very quick response and no oscillations at steady state. On the other hand, the system is borderline unstable. A small change in the characteristic of any of the components of the system (e.g. due to temperature, change in component values etc.) will make the system oscillate. Operating with such low margins should be avoided.


Examples of good compensation
Underdamped
Below examples of proper loop compensation settings are shown. The phase margin is 46degrees and the gain margin 7dB. The response is slightly underdamped, as with a small overshoot and undershoot observed.


Critically damped
As can be seen below, with a small tweak in the compensation values, the response now exhibits critical damping. Observe that the overshoot and undershoot levels are higher compared to when the controller had very small margins. However, these increase margins ensure that the controller will not become unstable, even with small change in the converter component values.